Last week, a profile on a revenge porn website was created for a woman who lives in Maricopa County, Arizona. Many sexually explicit photos and a couple of videos are posted of this young woman, along with links to her social media accounts, and her place of employment. After all, this was posted a couple of months Arizona made posting revenge porn a felony in the state.
I might be jumping the gun (because many of these laws are only a week or two old), but I do not think the revenge porn laws offer effective deterrence. Instead the laws are pushing revenge porn underground into the “deep web” (I will define later) that will be next to impossible for law enforcement to track.
Also, I want to go on record that many if not all of the revenge porn laws only deal with half of the issue. Revenge porn is certainly a problem, but then personally identifying information is posted along with the photos that are used to destroy lives. The photos are one thing. Posting one’s place of employment, phone numbers, information about friends and family, are arguably just as much as the problem as the pictures themselves.

*** I do not condone, nor am I in favor of revenge porn in the least. It is de-humanizing and often results in intentionally destroyed lives, as I tried to illustrate in the screenshot above. But I do think these laws are going to be largely ineffective with how certain parts of the internet are becoming more and more anonymous.
So far in 2014, 11 states have enacted revenge porn laws: Arizona, Colorado, Georgia, Hawaii, Idaho, Maryland, New York, Pennsylvania, Utah, Virginia, and Wisconsin. California was ahead of the game and passed revenge porn legislation in 2013.
This post is going to get a little technical and refer to the “deep web” and the “clear web.” But I hope to make the point that revenge porn is now going underground and is going to be very difficult, if not next to impossible for law enforcement
What is Revenge Porn
Revenge porn is a degrading and dangerous pursuit. The posting of nude and sometimes explicit pictures is only half of the problem. The other half is users post, accompanying the photos, dates of birth, links to any and all social media accounts that can be found (facebook, twitter, linkedin, pinterest, etc), places where the individual works, and/or sometimes phone numbers. Then, what I believe is a small minority of users on these websites, try to create havoc. Often times this mob will email and any all contacts of the person whose pictures are posted.
It is unlawful to intentionally disclose, display, distribute, publish, advertise or offer a photograph, videotape, film or digital recording of another person in a state of nudity or engaged in specific sexual activities if the person knows or should have known that the depicted person has not consented to the disclosure.
— Ariz. Rev. Stat. § 13-425 (A).
The law has good intentions and tries to resolve a growing problem.
The law is only effective if you can trace who put them up online. That is becoming harder and harder to do because revenge porn operators, suppliers (the individuals supplying the pictures and seeking revenge) will want to keep as anonymous as possible. This is best done through the deep web.
The Deep Web
I am not a computer expert (period, end of sentence). The “deep web” although has been around for a while, it is just starting to get more user friendly. Additionally, with much more of the general population becoming privacy-minded in their online activities, more and more people are using the “deep web.”
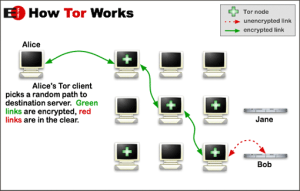
Tor makes it possible for users to hide their locations while offering various kinds of services, such as web publishing or an instant messaging server. Using Tor “rendezvous points,” other Tor users can connect to these hidden services, each without knowing the other’s network identity. This page describes the technical details of how this rendezvous protocol works.
A hidden service needs to advertise its existence in the Tor network before clients will be able to contact it. Therefore, the service randomly picks some relays, builds circuits to them, and asks them to act as introduction points by telling them its public key. Note that in the following figures the green links are circuits rather than direct connections. By using a full Tor circuit, it’s hard for anyone to associate an introduction point with the hidden server’s IP address. While the introduction points and others are told the hidden service’s identity (public key), we don’t want them to learn about the hidden server’s location (IP address).
— Tor: Hidden Service Protocol
For our purposes TOR (The Onion Router) acts in two main ways. 1. It can make the internet surfer largely anonymous. 2. It can make TOR hosted websites (.onion) largely anonymous.
Free speech advocates, drug dealers, hit men, and coffee drinkers (Dark Net Roasters) all use the deep web, websites to keep their anonymity. I really don’t like my coffee with a side of NSA surveillance.
Some think the United States government has cracked the “deep web” and removed the anonymity. Even if they did not crack the deep web, they are trying. Russian President Vladimir Putin two weeks ago offered $110,000 reward for cracking TOR as usage skyrockets in the country.
More and more of the revenge porn websites are going to go to the deep web to stay anonymous as long as possible.
Final Thoughts
I think law enforcement is going to have a tougher time trying to enforce this law, especially if revenge porn websites continue to move to the deep web. Also, I think the harassment from posting the personal identifying information is just as problematic as the nude photos.
It will be interesting to see how the law will be implemented.
I assume this is where those looking for child sex find it. Instead of LE placing ads on adult sites like BP, which violates terms of service for underaged, LE places an escort ad with an adult age, with fake pictures of adults and then entraps guys and arrests for child prostitution. I assume if they wanted to find and arrest men that actually ARE looking for underaged they could somehow find it on this dark web. But seems they only do it by entrapment on adult sites, pretending to be adults.
Even if they can’t trace on the dark web they could set up sting appointments just like they do on BP… but actually find men that seek children, vs those seeking adults that are tricked into child prostitution.
Hi Dave,
Again, I am not a computer expert. I just wanted to get a discussion going about the efficacy of revenge porn laws. I am not sure how similar or dissimilar the law enforcement tactics would be for monitoring and tracing revenge porn, as they do for child porn. I have heard that quite a bit of the deep web is used for child porn. Additionally, I have heard the hacktivist group Anonymous take a stand against child porn on the deep web and try to disable websites that distribute child porn, where law enforcement was unable to or did not know about. The deep web is really the wild west of the internet, and I do not know how effective law enforcement can and will be when it comes to revenge porn.
oops “Deep web” not “dark web”